 |
| Credits to image Wikimedia
what's topology , its types, and the way they differ from each other .
Network topology is how computers connect/relate to at least one another during a network .
It is of two types:
Physical topology describes the way computers connect with the assistance of cables.
Logical topology describes the way data flows from one computer to a different within a network .
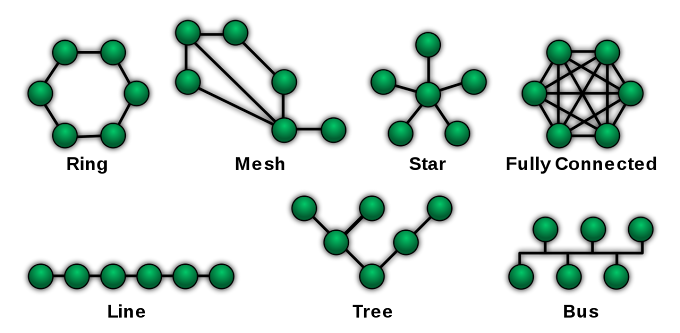
The most common network wont to interconnect physically distributed computers is Local Area Network which has three main topologies:
star
bus , and
Ring Topology
Others are:
mesh , and
Hybrid Topology
Please note, the info within the network layer is within the form IP packets. IP packets are packed into frames within the link layer. Physical layer then transmits the frames into the transmission media.
For example, networking cables. So during a network , the info moves from one computer to a different within the sort of frames. an equivalent term are going to be utilized in further discussion.
1. bus topology
bus topology , computers hook up with a shared central cable, called a bus, with taps and drop lines. Shared means all connected computers use an equivalent cable for data frame transmission.
Taps are the connectors, and drop lines are the cables running in between the computers and therefore the bus.
In this topology, if a computer sends data frames to a second computer, all other computers connected to an equivalent central cable also receive the frame.
i.e. other computers can hear what the primary computer is saying. However, only the target computer accepts it; others reject the frame by checking the destination MAC address within the received frame.
Since bus requires less cabling, so it's easy to put in and fewer expensive to implement as compared to other topologies.
However, with the rise within the length of the central cable and increase within the count of taps, the strength of the signal decreases, so only a limited number of computers are often connected in bus .
In this topology, all computers depend upon the central cable for data transmission. So, if the central cable fails, it paralyzes the entire network,
i.e. bus has little or no fault tolerance. Here, a security risk also exists because all computers can hear what other computers are saying on the shared media.
In a bus , just one computer can transmit data at a time. So while one computer is sending a file to a printer, other computers need to wait.
If other computers too start sending data at an equivalent time, it'll collide and corrupt the entire data. In such a case, data should be re-transmitted.
Therefore, if more computers hook up with an equivalent central cable, the network will become slower and also increase the probabilities of knowledge collisions.
It is one among the explanations why bus is never utilized in modern computer networks. The collisions are often avoided by using an access control protocol.
2. star topology :
star topology , the computers hook up with a central device, a switch or a hub, with point-to-point communication links.
Point-to-Point connection means there's a fanatical link/cable between the 2 devices. Other devices can't use it.
In this topology, if one computer wants to send some data frame to a different computer, it's first routed to the central device.
The central device, then, either broadcast or unicast the received data frame towards the destination computer supported the sort of central device used.
Broadcast means the transmission of knowledge to all or any connected devices while unicast means transmission of knowledge to the target device only.
If the central device may be a hub, it broadcasts the received frame to all or any of the connected computers,
i.e. a hub may be a multiport repeater. The frame features a destination MAC address which is exclusive to each computer present during a network, so only the target computer accepts the frame, others reject it.
Since a hub broadcasts the received data, so it increases unnecessary data traffic within the network. to beat this limitation, a switch is employed as a central device. Every computer features a unique MAC address.
A switch stores the MAC address of the devices connected to its ports. it's called a switch table.
Suppose your computer is connected to a printer with a star network. Now, you click on PRINT on your computer to print a file. The file is shipped to the central device. If the central device may be a hub, the file is forwarded to all or any the connected computers. However, only the printer accepts it.
In star topology , just one input/output port and one cable is required for every device to attach to many devices.
It makes it less costly than the mesh .
It is also easy to reconfigure because we will add or remove devices just by connecting or disconnecting one cable.
If one cable connecting to the central device fails, just one communication link goes down and not the whole network.
So star topology has good fault tolerance.
Fault detection is additionally easy because we only got to locate a computer which isn't receiving data.
However, If the central device goes down, the entire network is paralyzed.
One more limitation in star is that the number of computers within the network is restricted by the amount of input/output ports within the central device.
Example of star High-speed LANs. Now Ring topology during a ring topology, each computer connects to 2 computers to make a hoop . Data transmitted by one computer moves from one computer to a different during a circular fashion to succeed in its final destination.
3. Ring topology
the advantages of ring topology are Easy installation and fewer cabling, compared to mesh .
In this topology, data moves in one direction, it reduces the probabilities of knowledge packet collisions. The ring topology is comparatively easy to troubleshoot because we only got to locate a computer which stops receiving data from its upstream neighbour.
However, As each data frame has got to pass all computers between the source and destination, it makes data transmission slower than the star .
Since all computers hook up with form a closed-loop system , one fault paralyzes the entire network. it's difficult to reconfigure because we'd like to interrupt the ring to feature or remove the computers.
Due to this reason, the physical ring topology is never used, instead logical ring topology is employed .
Example of ring topology is Token ring Token Ring doesn't use a physical ring topology. Instead, it uses a physical star and logical ring topology during which the info moves during a circular fashion.
Token ring uses a token-passing protocol, where a frame, called token, keeps on circulating on the ring. If one computer has data frames to transmit, it holds the token and transmits the frame.
Once the transmission is completed , the token is released into the network. A token ring network is deterministic, meaning each connected computer is given access for transmission at fixed time intervals.
Therefore, a network can have one topology and a completely different topology at an equivalent time. mesh during a fully connected mesh , each device features a point-to-point link to each device within the network.
If the amount of devices during a network is 4 · Then the amount of links/cables each device have is 4-1, i.e. 3 Now, we've 4 devices,
Total number of links/cables 4 devices have is 4 (4-1), i.e, = 12 Note that these are simplex links. In simplex links, data can move in one direction only.
So, one link is employed for sending data, and therefore the other is employed to receive data from the adjacent computer. Duplex links are those where data can move in both directions.
Therefore, we will replace two simplex links with one duplex link. Hence, the entire number of duplex links within the mesh is 4(4-1)/2, i.e. 6. generally , if there are n devices, the entire number of simplex links are n (n-1), the entire number of duplex links are n (n-1)/2, and therefore the total number of input/output ports in each device is n-1.
If the entire number of computers to be connected is 10, then the entire number of duplex links are going to be 45, and every device should have 9 input/output ports, which might be difficult to manage and also increase the value . However, The dedicated point-to-point link eliminates traffic problems which are encountered if a link is shared among several devices.
The dedicated point-to-point link maintains privacy and security of the messages shared between two devices because other computers cannot hear what the pc A is saying to computer B.
If one link fails, it doesn't affect the entire network, i.e. good fault tolerance, · Since each device is connected to each device, so installation is difficult.
If the total number of computers to be connected is 10, then the total number of duplex links will be 45, and each device should have 9 input/output ports, which would be difficult to manage and also increase the cost. However, The dedicated point-to-point link eliminates traffic problems which are encountered if a link is shared among several devices.
The dedicated point-to-point link maintains privacy and security of the messages shared between two devices because other computers cannot hear what the computer A is saying to computer B.
If one link fails, it does not affect the whole network, i.e. good fault tolerance, · Since each device is connected to every device, so installation is difficult. · Multiple input/output ports and a large number of cables increase the cost and make it expensive. · More cables in mesh topology consume large space too.
Example of mesh topology is The connection between regional telephone offices. All topologies are interconnected to form a hybrid topology. Every topology has it’s merits and demerits, so while choosing a physical topology for a network, we should always consider: It's Cost Ease of installation Ease of maintenance, and Cable fault tolerance.
|
Topology of network | topology types
Śübhäśh7
March 28, 2020
Search This Blog
Featured post
 website
website
What is DoS and DDos Attack | 2020
April 20, 2020
Popular Post
Recent Posts
3/recent/post-list
Popular Posts
Menu Footer Widget
All the Copyright by 99cybersecurity | Created by Kishan and Subhash






0 Comments
Please do not enter any span links in comment box